Cybersecurity, often known as information security (InfoSec), describes the procedures and tools used to protect digital data and systems against unwanted access, use, disclosure, disruption, alteration, or destruction. This involves safeguarding private or confidential information kept in both digital and physical versions, as well as sensitive data including financial and personal information. To guarantee successful information security, a thorough and multidisciplinary approach is necessary, integrating people, procedures, and technology to build a strong defense against potential attacks.
This blog, written by the experts at AllAssignmentHelp will discuss information security’s types, uses, and strategies for safeguarding our sensitive data.
What is Information Security?
Information security involves more than merely protecting sensitive data from inquisitive eyes. Data must be safeguarded using a range of techniques to prevent unauthorized use, disclosure, interference, alteration, inspection, recording, and destruction. For example, biometric data, data from mobile devices, and private information from social media platforms can all fall under this category. Because of this, information security is a wide topic that crosses several academic fields, including online social media, mobile computing, cryptography, and cyber forensics, to mention a few.
Effective information security requires a complete comprehensive plan that also considers technology, people, policies, procedures, and other aspects of the other information environment. Maintaining the monitoring, assessment, and modification are also essential mainly for managing the emerging vulnerabilities and threats.
Be it information security or cyber security, both are quite challenging when it comes to assignment writing. To help you approach the subject better you can take advantage of online cyber security assignment help service. This can be highly beneficial in attaining higher grades and easing the academic pressure that students go through during their entire college phase.
Read more: Data Security and Cyber Threats
Objectives of Information Security
Technology has advanced to emphasize information safety and security to safeguard our best interests. Ensuring information’s confidentiality, integrity, and availability (CIA) is one of the main objectives of information security programs.
Here are these objectives in brief:
Confidentiality
Protecting sensitive information from being disclosed to unapproved parties, groups, or procedures without the required authorization or approval is the goal of confidentiality.
Integrity
It refers to preserving the accuracy and comprehensiveness of data. This implies that illegal editing of data is not possible. To ensure that data is correct and comprehensive, for instance, if an employee quits the company, all departments’ records for that person, such as accounts, should be updated to reflect the employee’s status as JOB LEFT. Only authorized personnel should also be able to alter employee data.
Availability
It requires that information be accessible when required. For instance, obtaining information about a specific employee to determine whether they have taken more time off than expected would necessitate coordination between various organizational teams, including network operations, development operations, incident response, and policy/change management.
Apart from this, a few more principles govern IT Security programs.
These are:
Non-Repudiation
According to this, no party may contest receiving a communication or transaction. Furthermore, neither you nor the other party may retract the message or transaction. In the realm of cryptography, for instance, proving that the message corresponds with the digital signature created using the sender’s private key is sufficient. Furthermore, no one else could have changed the message that was sent during transmission. Non-repudiations require data validity and integrity.
Authenticity
It entails confirming that individuals claiming to be from reputable sources are. Furthermore, every input that reaches a destination comes from a reliable source. This principle ensures that the communication is authentic and legitimate and comes from a reliable source via a legitimate transmission.
Accountability
This says that an entity’s actions ought to be able to be traced back to it specifically. For instance, as we covered in the Integrity section, not all employees earn the ability to alter the data of other employees. An organization should designate a distinct department with full responsibility for making changes of this nature. Should they receive a request to modify the data, a higher authority’s signature is required on the letter. For instance, the organization’s director. Furthermore, the individual assigned to make these modifications does so after thoroughly checking each detail about the person. such as their fingerprints, etc.
The act of preserving CIA information, or making sure that information is not compromised in any way when crucial situations arise, is at the heart of information security. Natural calamities, server and computer breakdowns, etc. are not the only problems that these arise from.
Advantages of Information Security Implementation
There are a handful of pros to the successful implementation of the InfoSec program in a company or business.
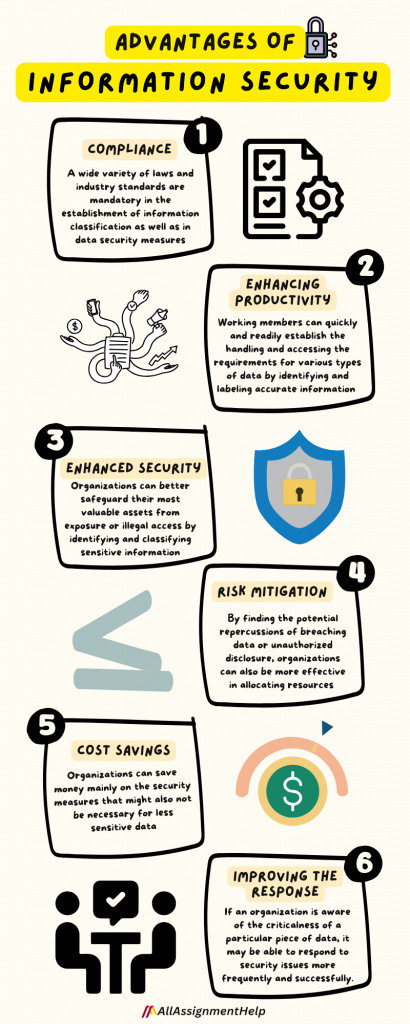
Let’s have a look at these below:
Compliance
A wide variety of laws and industry standards, such as PCI-DSS and HIPAA, are mandatory in the establishment of information classification as well as in data security measures.
Enhancing productivity
Working members can quickly and readily establish the handling and accessing the requirements properly for various types of data by identifying and labeling that information accurately.
Enhancing security
Organizations can better safeguard their most valuable assets from exposure or illegal access by identifying and classifying sensitive information.
Enhancing mitigation of risk
By finding the potential repercussions of breaching data or unauthorized disclosure, organizations can also be more effective in allocating resources and planning for the incident response.
Cost savings
By putting those in the place where the right security takes control of the different kinds of information they are managing, organizations can also save money mainly on the security measures that might also not be necessary for less sensitive data.
Improving the response to occurrence
If an organization is completely aware of the criticalness of a particular piece of data, it may also be able to respond to security issues more frequently and successfully.
Understanding how the implementation of InfoSec takes place is itself a vast chapter and students need to attend multiple classes to get a grab of it. Suppose, you have an assignment to work on and also have a class in the next seven hours on InfoSec implementation, you may think Is there anyone to take my online class for me as I need to complete my assignment urgently. The answer is YES! Many companies are offering online class help services at any time of the day and a pocket-friendly cost. Students can find and approach them through Google.
Read more: Information Security Analysts
Disadvantages to Implementing Information Security
There are some potential disadvantages to implementing an information classification system in an organization’s information security program.
Let us take a quick look into these as well:
Cost
Implementing and maintaining an information classification system can be costly, especially if new software or hardware is required.
Inaccurate classification
People frequently classify information, thus it’s probable that some content will be incorrectly categorized. This could result in inadequate security or pointless access limitations.
Lack of adaptability
Information classification systems may be hard and unyielding, making it challenging to adapt to new data kinds or shifting business requirements.
Opposition to change
If an information classification system is implemented, some employees can object, particularly if it means they will have to adjust their regular work schedules.
A delusion of safety
Establishing an information classification system may provide businesses with a sense of security so great that they may overlook other essential security measures and industry best practices.
Maintenance
Information classification should be regularly examined and updated to avoid it becoming stale and useless.
Complexity
Establishing and maintaining an information classification system can be challenging and time-consuming, especially for large organizations that handle a wide range of data types.
Everything has its negative effect and the same applies to InfoSec as well. To be able to comprehend what will work and what will not, students have to have a deep understanding of every component associated with Information Security. However, to have such a crystal-clear idea they need to devote maximum time to learning these things. But assignments and online classes chomp off a lot of time. In this situation, one who is eager to know the in-and-out of InfoSec wonder, I wish I had someone to take my online exam for me. This would help me give more time to learning bits and pieces related to InfoSec.
The good news is that, with just a few clicks they can find online exam givers based in your region. Connecting them can give students like you much time to invest in better and deeper learning.
Uses of Information Security
Breaches are occurring like never before and companies are always trying to safeguard their information. This is one of the sole reasons behind the vast use and implementation of InfoSec irrespective of sector and organization size.
Information security has many uses, including:
- Privacy: The preservation of sensitive data’s privacy and security against unauthorized access is referred to as confidentiality.
- Risk Management: It is the practice of identifying and mitigating potential security threats to protect the business.
- Integrity: Preserving the consistency of the data and correctness in the face of malevolent attacks.
- Disaster recovery: It is the process of generating and putting into action a plan for the recovery promptly from the loss of data or system malfunctions.
- Encryption: The safe encoding of personal information for guarding against unauthorized access.
- Availability: Ensuring that all the information required by approved users is also accessible when needed.
- Network Security: The practice of defending computer networks mainly from theft, unauthorized access, as well as any other threats is known as network security.
- Compliance: Adhering to the legal as well as regulatory standards, including those relating to data protection and privacy.
- Authenticity: Verifying a user’s identity before granting them access to a data system is known as authentication.
- Physical security: It is the procedure of securing the real structures that the cluster of information systems are available for guarding against data loss, theft, or damage.
The use of InfoSec is becoming highly popular and for some businesses a must in the present times.
List of institutes offering courses in information security in the USA
Many institutes spread across the USA that offer online as well as offline degrees in information security.
Take a look at some of the popular ones below:
- George Washington University
- University of California
- Mississippi State University
- Northeastern University
- Southern Methodist University
- Temple University
Information Security courses in other countries
There are colleges in European countries that offer a great opportunity to get a degree in Information security.
Take a look at some of the prestigious ones below:
- IU International University of Applied Sciences
- Aalborg University
- National College of Ireland
- University of Limerick
- Dublin City University
- KTH Royal Institute of Technology
All the above-mentioned institutes are great at offering courses in Information Security and have phenomenal instructors to help students achieve great success in it.
One subject that students often have to take along with InfoSec is statistics. This subject is highly scored but often poses critical issues. Many find difficulties in understanding statistical theories that are being discussed in offline or online classes. Students of traditional courses can still have the position to clear their doubts from their friends or professors at another time.
However, those pursuing an online course may not be able to get it as there is very little scope for meeting classmates or the professor in real time as everything is online. At this juncture, students often think, I wish I could pay someone to take my online statistics class for me. This is where online class takers can help students in lessening their academic issues. By shelling out a very small amount, students can get their online stats class attended by experienced experts. They can also get notes at the end of the session to understand what has been discussed in the class that day.
Information Security vs. Cybersecurity
While physical document security, facility access plans, and other facets of information security deviate from cybersecurity, information security is still a part of a broader cybersecurity strategy. But when it comes to safeguarding digital data, it’s critical to recognize the areas where the two intersect.
Information security in cybersecurity refers to safeguarding client data with secure login credentials and password management, implementing access control procedures, and encrypting data to prevent prying eyes and hackers from stealing or destroying it.
Read more: Data Security – Definition, Types, Importance, Common Risks
Conclusion
Every organization and business operates in a setting where they are subject to various risks in various contexts. Risks that many organizations deal with on a daily basis include financial risks, process-related risks, technology-related risks, personnel-related risks, and legal risks. Information security should endeavor to identify and control the dangers to which it is exposed, much like other risk management work does.
By implementing a methodical approach to information security, establishments can enhance the caliber and assurance of their functions. Increasing the likelihood of success in information security activities can be achieved by starting from established standards.
Frequently Asked Questions
| Question 1: What are the 3 main information security concerns? Answer: The main types of information security threats are – Malware attack Social engineering attacks Software supply chain attacks |
| Question 2: Why do we need information security? Answer: Information security protects sensitive information from unauthorized activities, including inspection, modification, recording, and any disruption or destruction. The goal is to ensure the safety and privacy of critical data such as customer account details, financial data, or intellectual property. |
